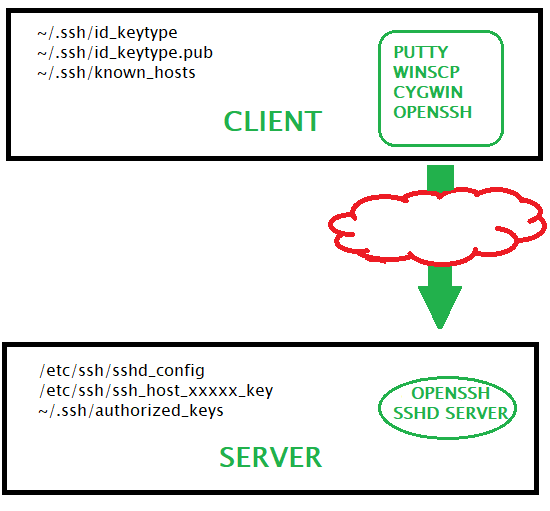
Sshd is the OpenSSH server process. It listens to incoming connections using the SSH protocol and acts as the server for the protocol. It handles user authentication, encryption, terminal connections, file transfers, and tunneling. Securing SSH Server. You can secure your OpenSSH server by setting the following options in the sshdconfig configuration file. X11Forwarding – Enabling X forwarding makes your system vulnerable to X11 related issues. So it’s a good idea to set it to no. PermitRootLogin – You should not allow root users to login directly to the system. You should always set it to no.
The OpenSSH SSH daemon supports SSH protocol 2 only. Each host has a host-specific key, used to identify the host. Whenever a client connects, the daemon responds with its public host key. The client compares the host key against its own database to verify that it has not changed. Forward secrecy is provided through a Diffie-Hellman key agreement. This key agreement results in a shared session key. The rest of the session is encrypted using a symmetric cipher. The client selects the encryption algorithm to use from those offered by the server. Additionally, session integrity is provided through a cryptographic message authentication code (MAC).
Finally, the server and the client enter an authentication dialog. The client tries to authenticate itself using host-based authentication, public key authentication, challenge-response authentication, or password authentication.
If the client successfully authenticates itself, a dialog for preparing the session is entered. At this time the client may request things like allocating a pseudo-tty, forwarding X11 connections, forwarding TCP connections, or forwarding the authentication agent connection over the secure channel.
After this, the client either requests a shell or execution of a command. The sides then enter session mode. In this mode, either side may send data at any time, and such data is forwarded to/from the shell or command on the server side, and the user terminal in the client side.
When the user program terminates and all forwarded X11 and other connections have been closed, the server sends command exit status to the client, and both sides exit.
Install the following Cygwin packages (rerun setup if necessary -- you can add packages after you have already installed Cygwin).
Admin --> cygrunsrv
Net --> openssh
Open a new bash shell window and run the SSH configure stuff.

Openssh Sshd Service
ssh-host-config -y
This step will create necessary configuration files, a priviledge separation user and necessary directories.
When prompted with 'CYGWIN=' type for following:
tty ntsec
Now you are ready to start the service.
cygrunsrv -S sshd
Finished
Sometimes you get a sshd/cygrunsrv service error after trying to run the service.
Openssh For Windows
cygrunsrv: Error starting a service:
QueryServiceStatus: Win32 error 1062:
The service has not been started.
There can be a couple of causes for this. The following may fix the problem (this is not an option on XP Home).
Solution 1.
Openssh Ssh-agent
You may have an old or corrupt installation of Cygwin. Try reinstalling. The following may also help:
cygrunsrv -R sshd
REBOOT (or use the Task Manager to kill all instances of sshd that may be running in the background)
run 'ssh-host-config -y' again.
This seemed to help on a few systems I worked on.
Solution 2.
Open an explorer window and use the 'Properties | Security' dialog and explicitly add 'Full Control' for the SYSTEM user to the following directories:
Start Openssh Server
C:Cygwin
C:Cygwinvar
C:Cygwinvarlog
Openssh Sshd
Hope that helps!
